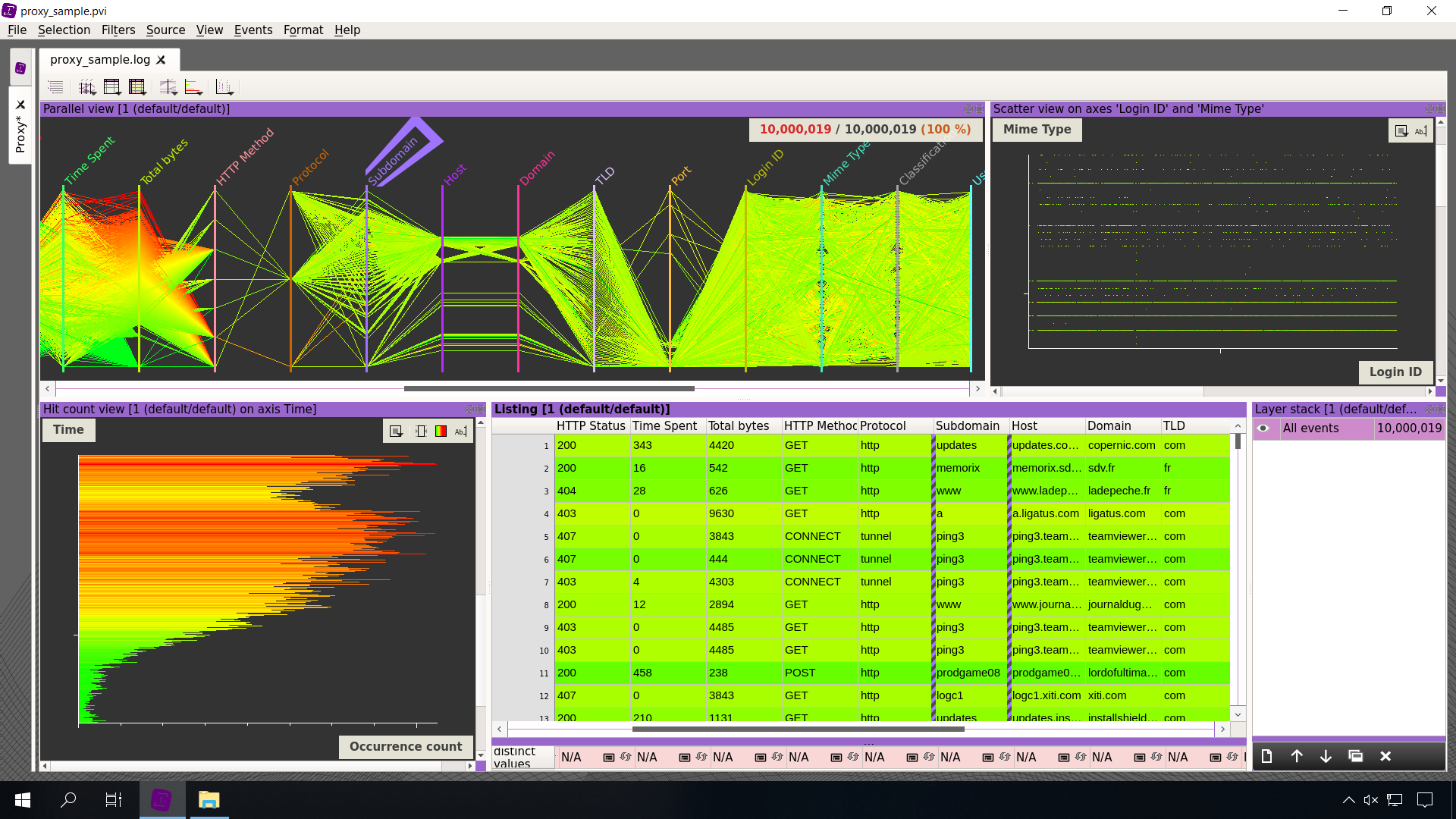
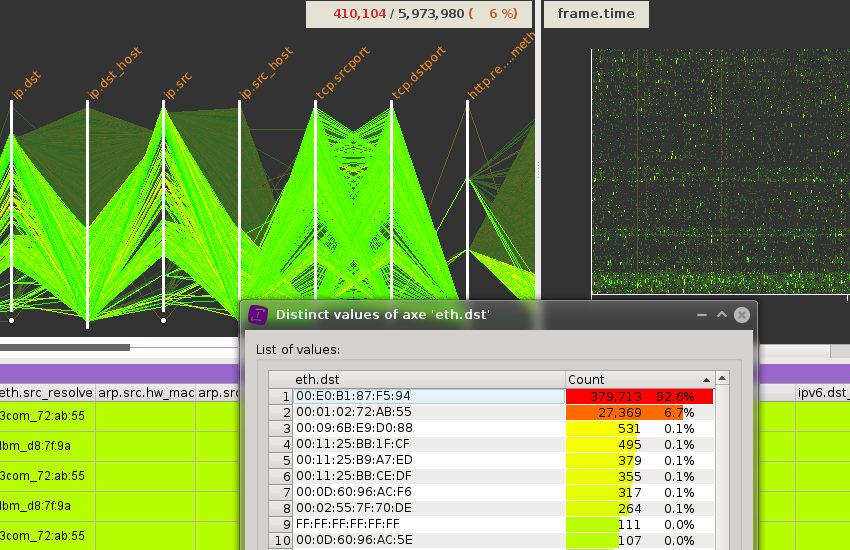
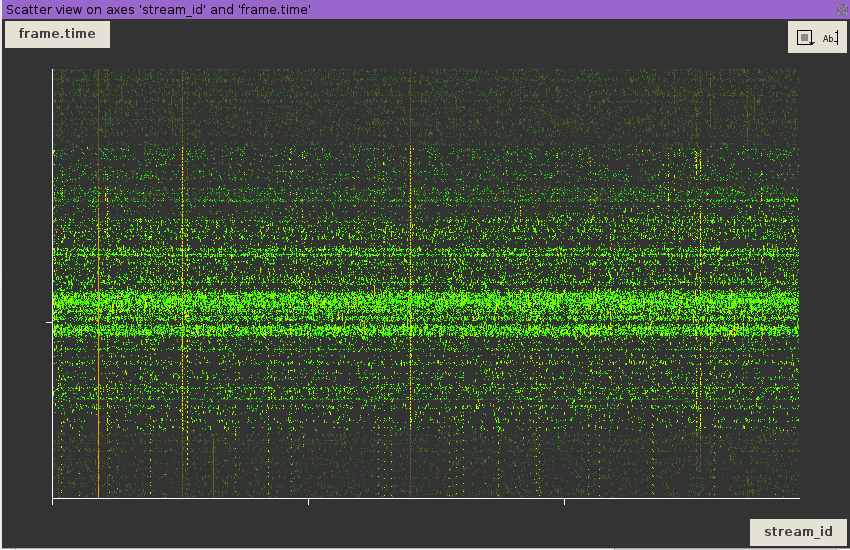
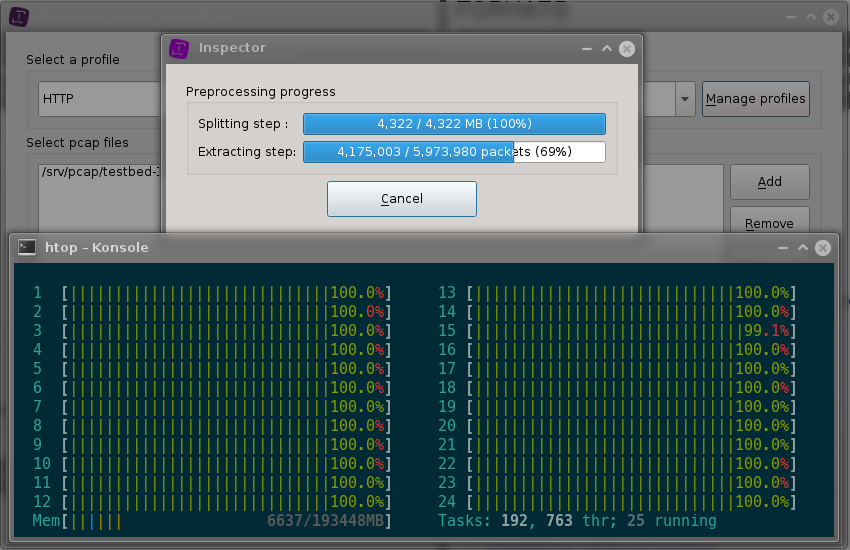
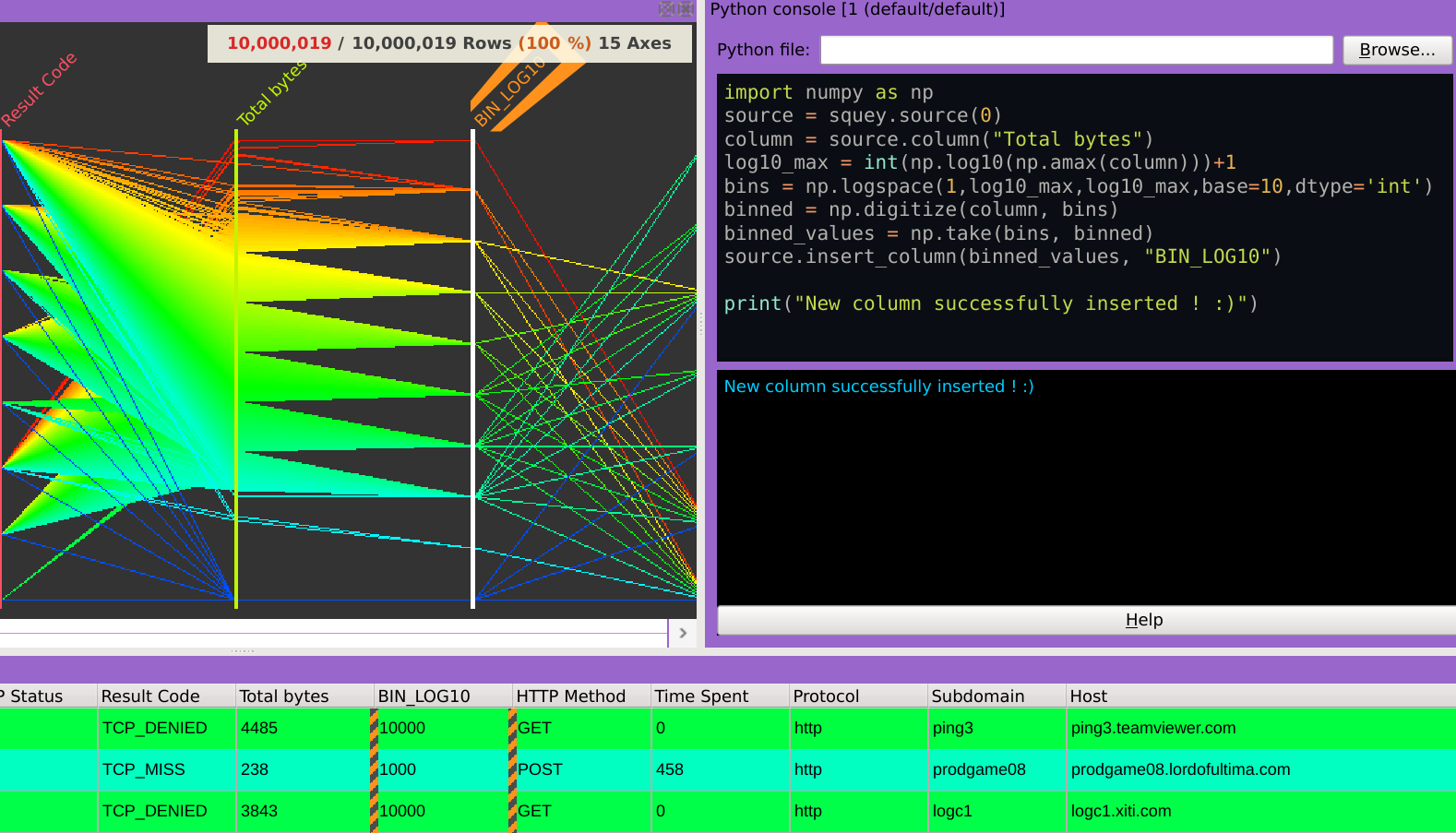
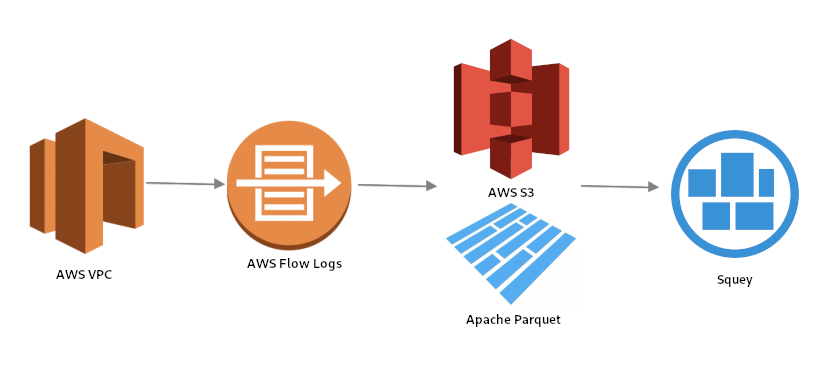
Assess data quality
🗸 invalid rows
🗸 invalid, incoherent or missing values
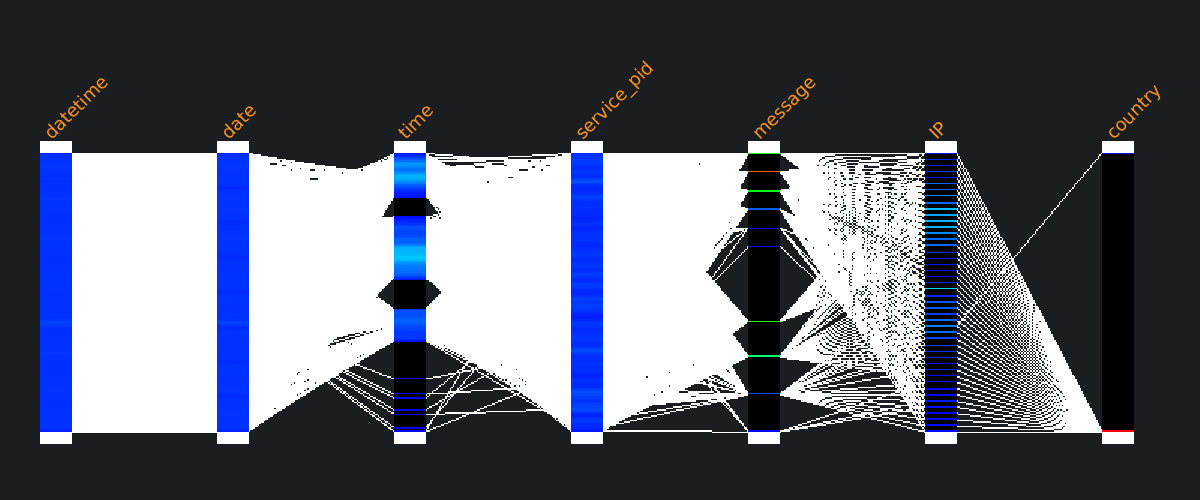
Understand data structure
🗸 Combine visualizations
🗸 Observe frequencies
🗸 Reveal outliers
🗸 Link multiple datasets