PentesterAcademy MACCDC 2012 DNS Challenge

Following a really small and easy challenge published on PentesterAcademy blog focused on the MACCDC 2012 DNS dataset analysed with ELK, we thought it could be an great exercice to guide you solving it using Squey.
Loading the dataset
Click on the Local files... button located on the SOURCES section of the start page and browse the compressed dataset.
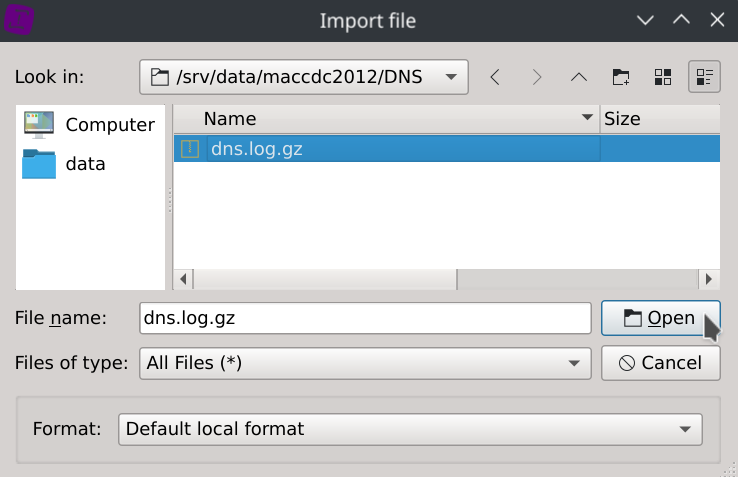
The file format and column types will be automatically detected, so just click Yes and Save.
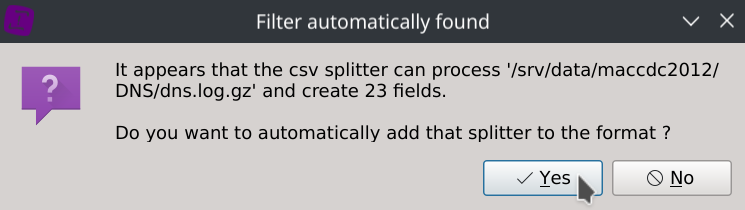
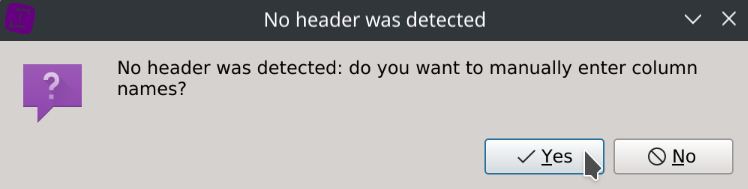
Unfortunately the dataset isn’t containing a header with column names but don’t worry, we got them from the dataset description:
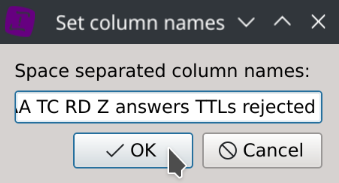
ts uid id.orig_h id.orig_p id.resp_h id.resp_p proto port query qclass qclass_name qtype qtype_name rcode rcode_name QR AA TC RD Z answers TTLs rejected
Choose Yes, paste the column names provided above, click Ok, then click Save.
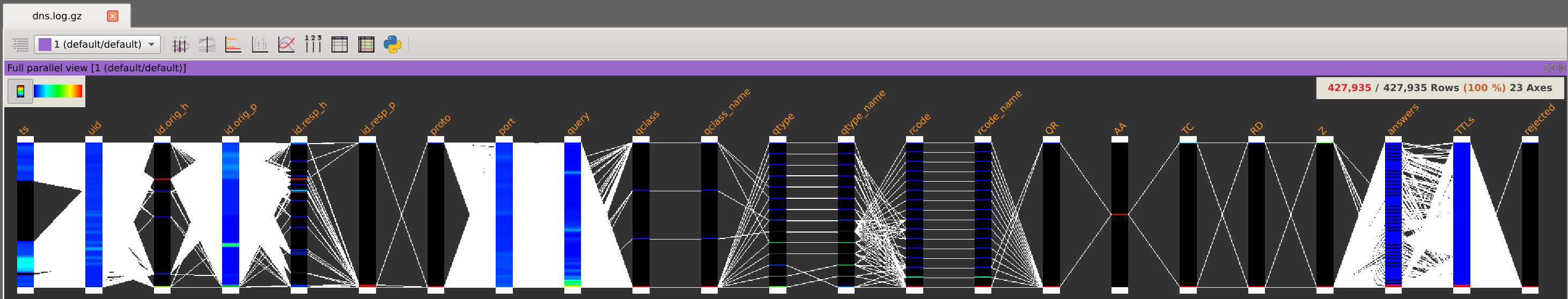
We now have the dataset loaded with the proper column names.
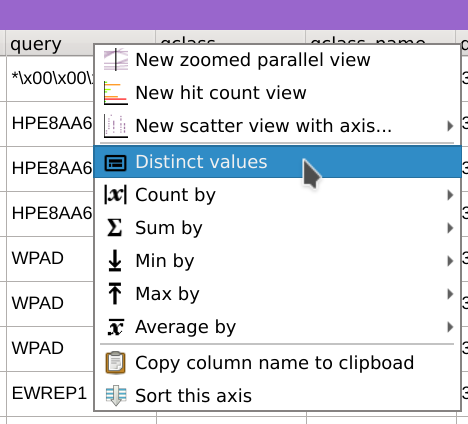
Q1. Provide the name of the most queried domain.
Right click on the query column header and select Distinct values.
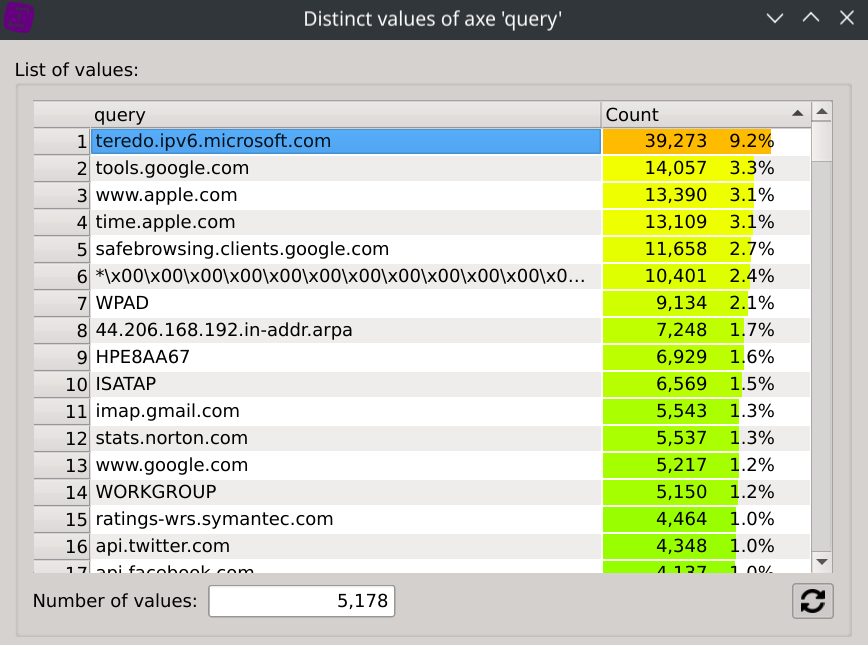
Answer: teredo.ipv6.microsoft.com (with 39,273 requests representing 9.2% of all requests)
Q2. What was the IP address of the machine which issued a maximum number of requests having empty DNS queries?
Select all events by clicking Selection menu and selecting select all events (or just press the a key).
Filter requests with empty DNS queries by right clicking on any value of the query column, select Search for..., paste the (empty) string and click Apply.
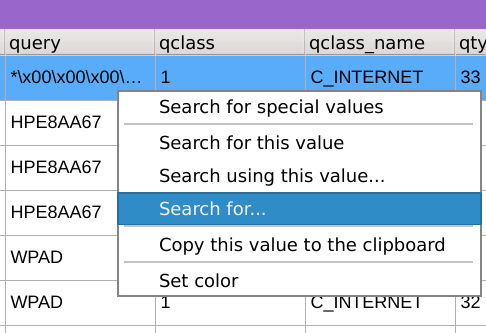
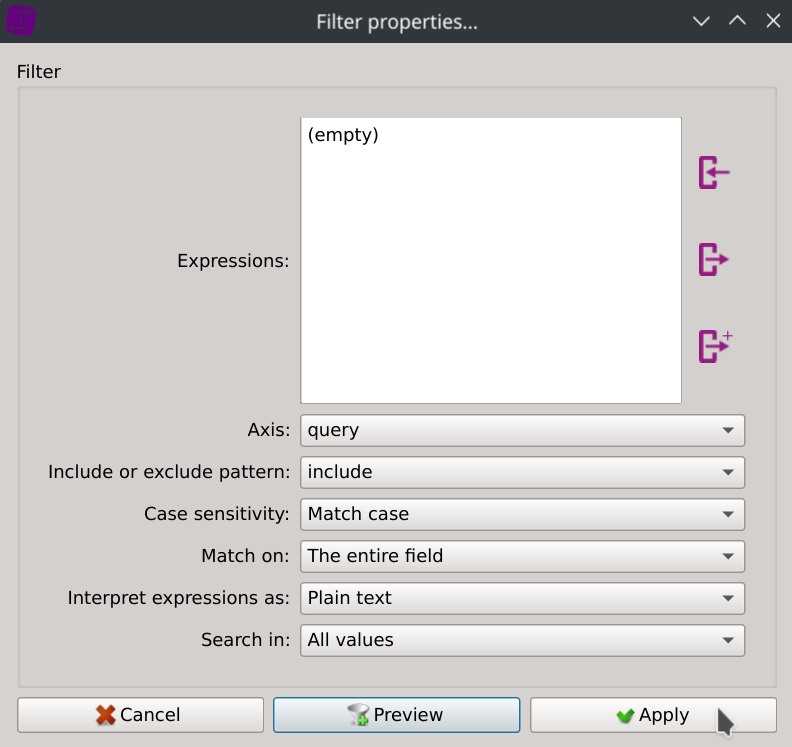
The dataset instantly got filtered and only empty DNS queries are now displayed.
Show IP repartition by right-clicking on the id.orig_h column header and selecting Distinct values.
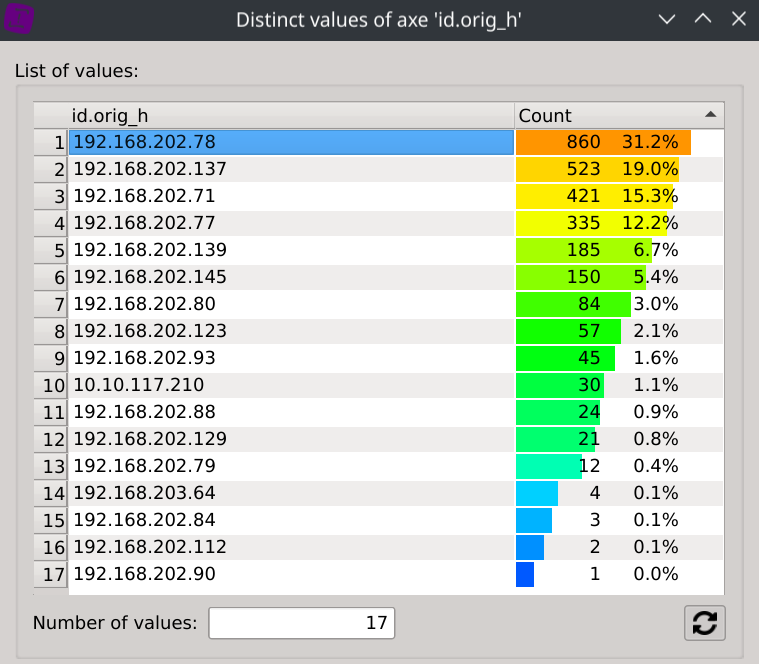
Answer: 192.168.202.78 (with 860 empty DNS queries representing 31.2% of all empty DNS queries)
Q3. What was the IP address of the machine that received a maximum number of NXDOMAIN responses?
Select all events.
Filter NXDOMAIN requests by selecting NXDOMAIN in the Distinct values dialog of the column rcode_name.
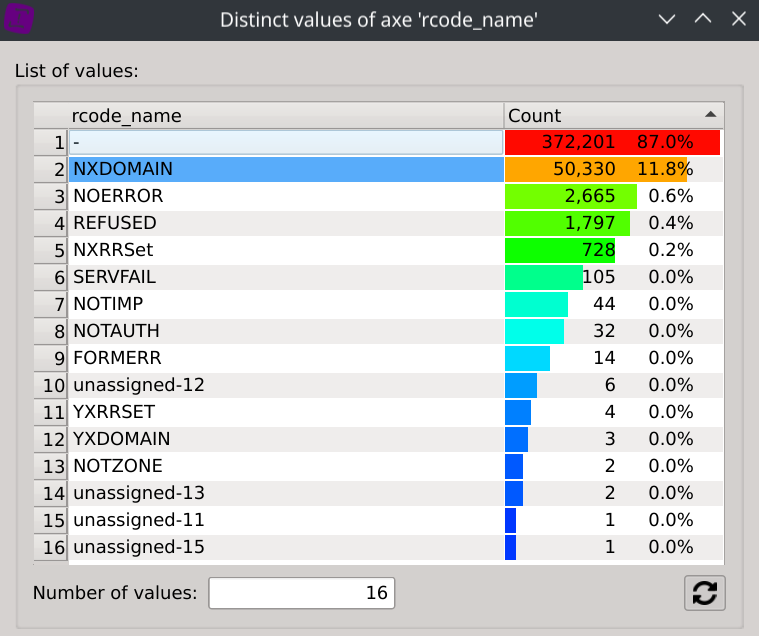
Show IP repartition by displaying the Distinct values dialog of the id.orig_h column.
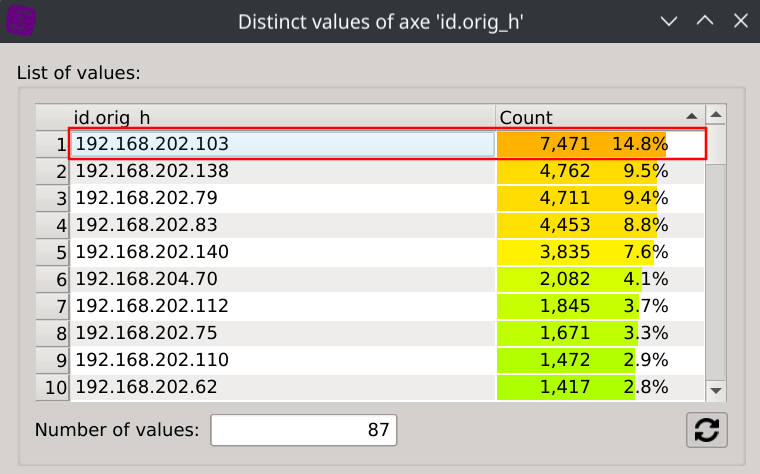
Answer: 192.168.202.103 (which received 7,471 NXDOMAIN responses, representing 14.8% of all NXDOMAIN responses)
Q4. For one of the hosts receiving NXDOMAIN errors, could you figure out some anomalous behavior? If yes, then describe the behavior.
As requests returning NXDOMAIN responses are still selected by previous question, we can directly show the repartition of target IPs and queries by displaying the Distinct values dialogs of both id.resp_h and query columns.
First, we can observe that the target IP 192.168.207.4 is generating 99.8% of all the NXDOMAIN responses (but it is also handling 62.3% of the total DNS requests).
Selecting the target IPs one after another will conveniently filter the distinct values of the query dialog so that you can easily see which domains are being considereded to be non-existant by the target IP.
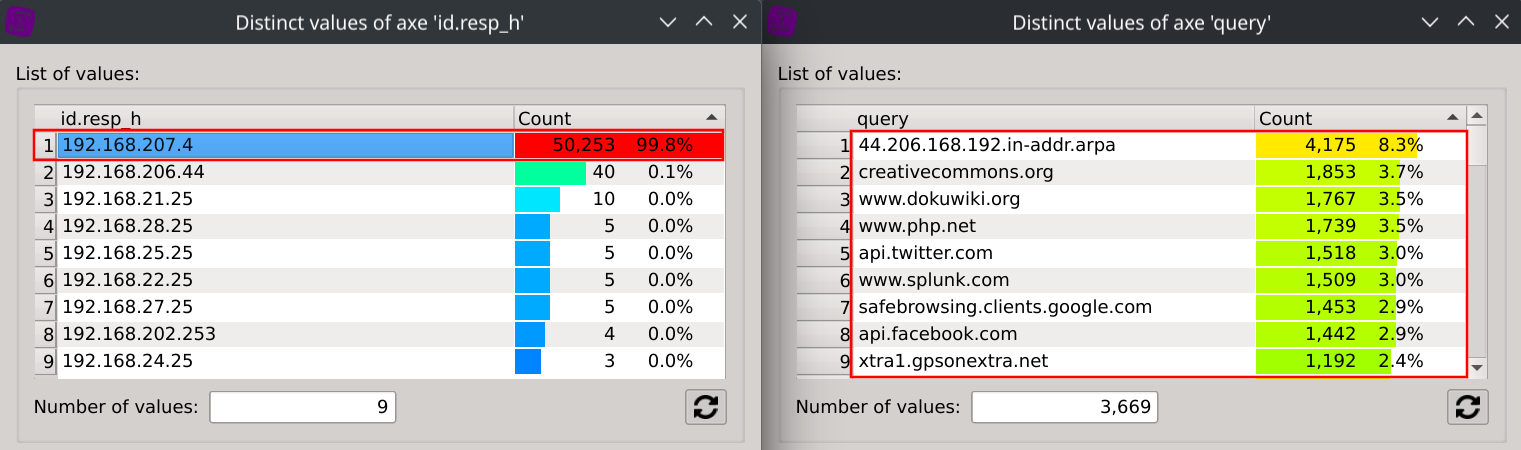
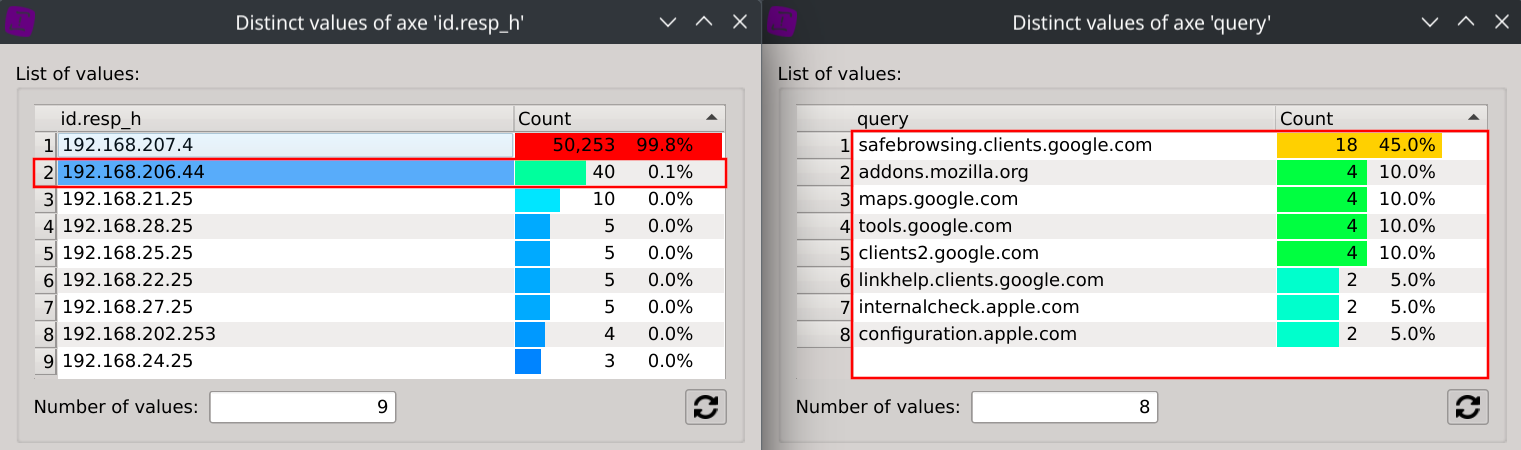
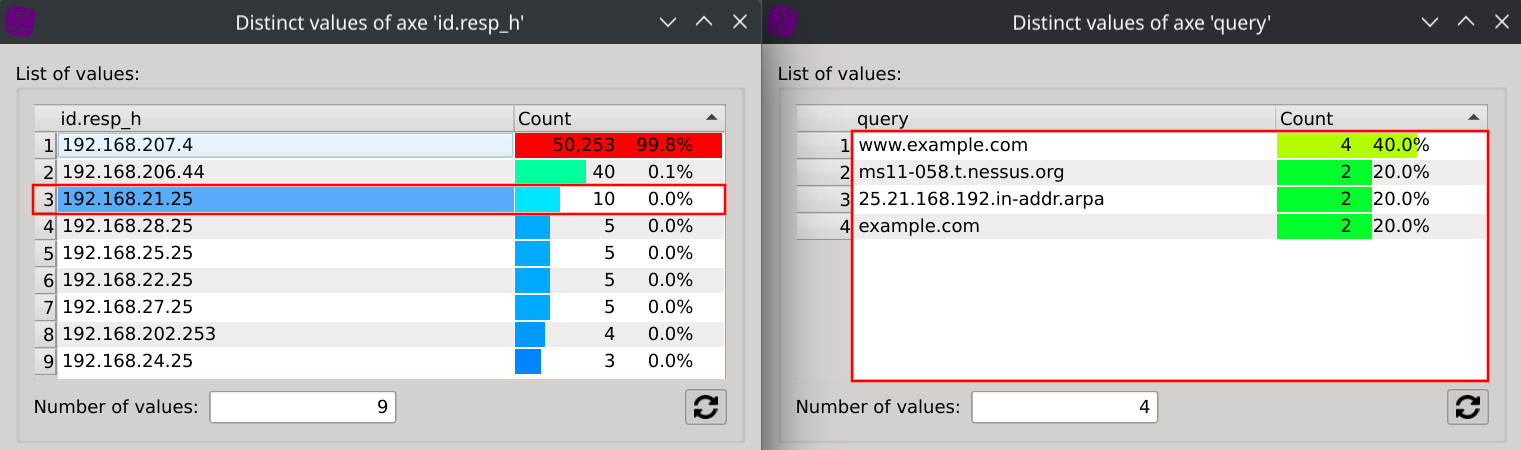
We can also filter all these 9 target IPs returning NXDOMAIN from the global dataset and observe their respective repartition of NXDOMAIN responses.
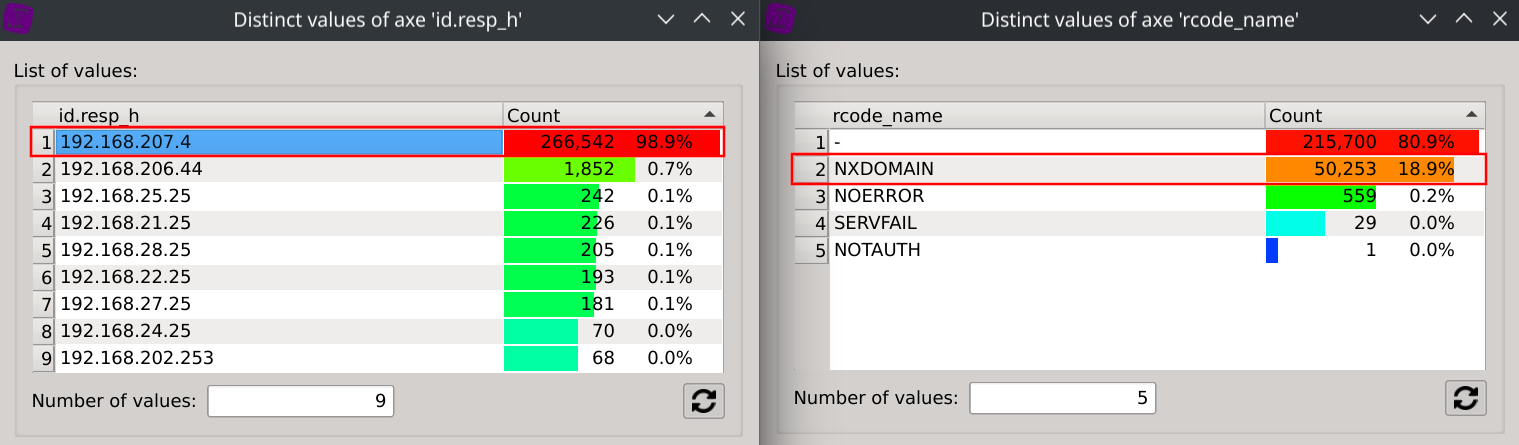
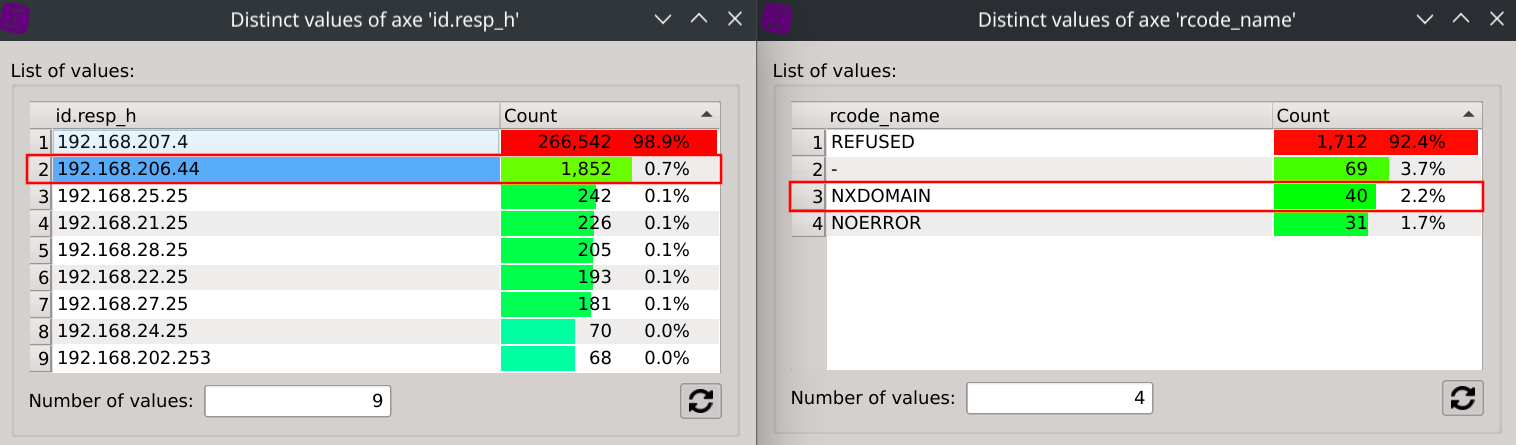
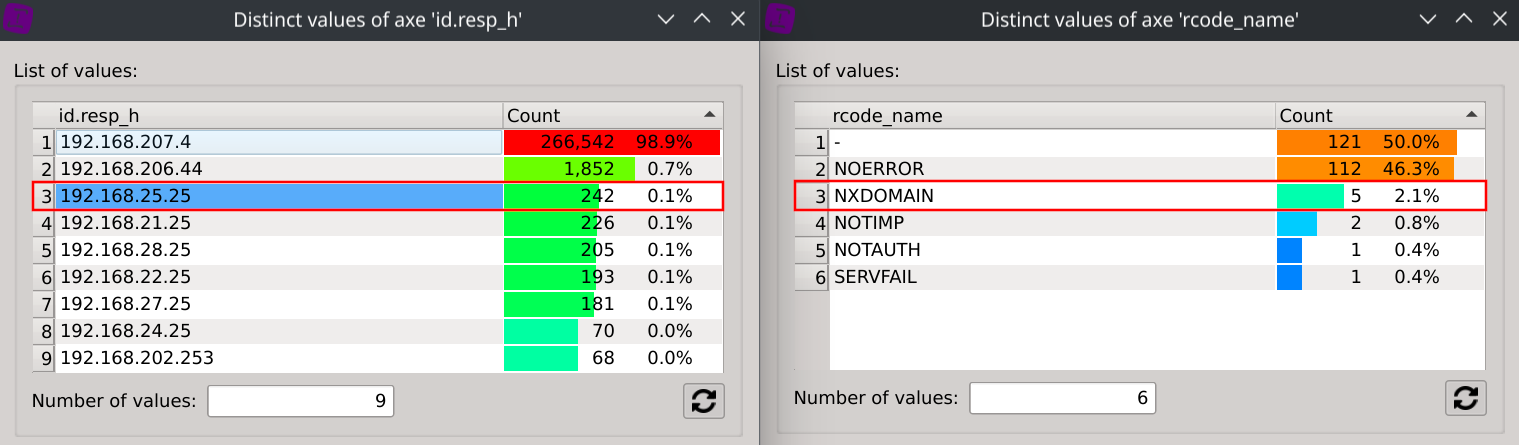
Answer: Some target IPs are wrongly returning NXDOMAIN for existing domains. Target IP
192.168.207.4is returning NXDOMAIN for 18.9% of its responses.
Q5. What was the IP address of the machine that sent the most DNS requests?
Select all events.
Show IP repartition by displaying the Distinct values dialog of the id.orig_h column.
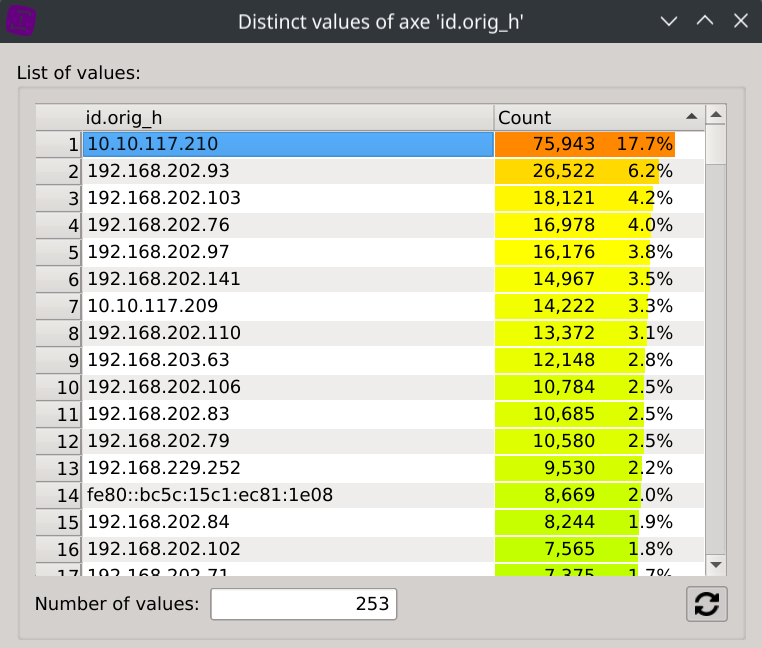
Answer: 10.10.117.210 (which sent 75,943 DNS requests representing 17.7% of all DNS requests)
Q6. What was the IP address of the machine that sent the most reverse DNS resolution requests?
Select all events.
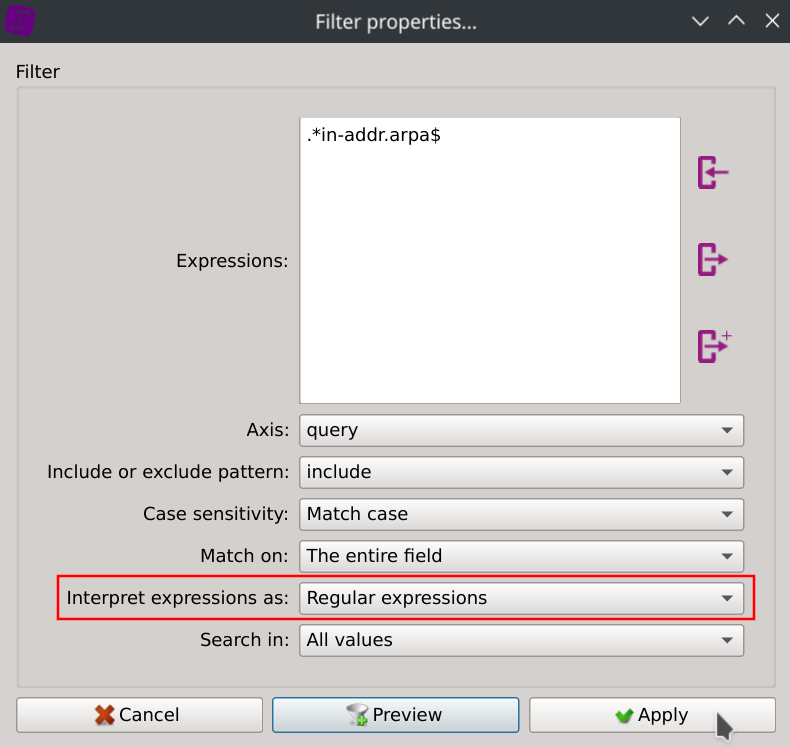
Filter reverse DNS resolution requests by entering the following regular expression in the search dialog of the column query
.*in-addr.arpa$
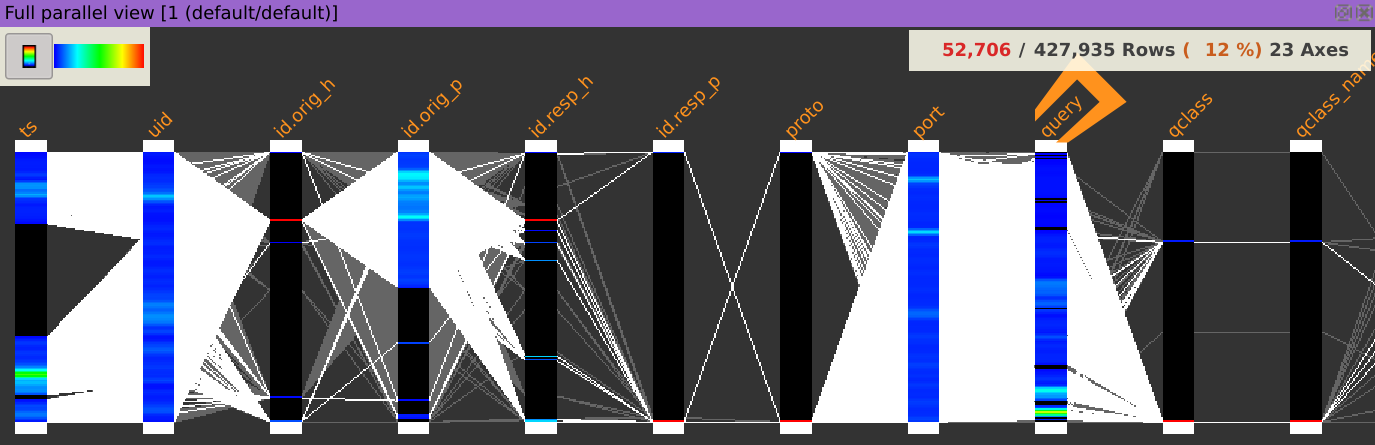
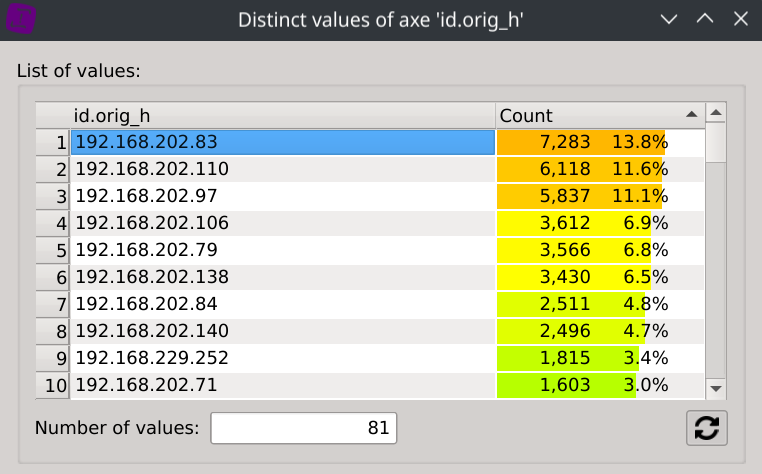
Answer: 192.168.202.83 (which sent 7,283 reverse DNS requests representing 13.8% of all reverse DNS requests)
Q7. How many DNS zone transfer queries were issued on the network?
Select all events.
Show query type repartition by displaying the Distinct values dialog of the id.orig_h column.
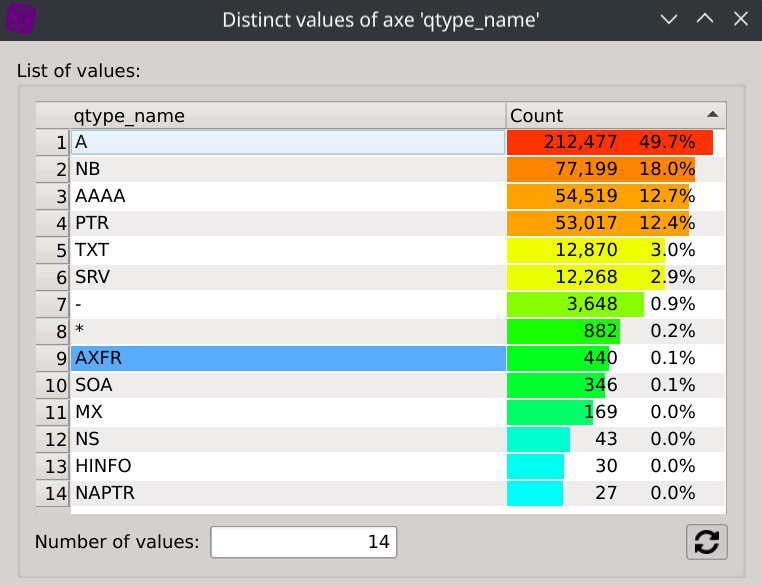
Answer: 440 (which represent ~0.1% all of DNS requests)
Q8. One of the DNS requests querying for a sub-domain of apple.com returned a TXT record which contained a suspicious-looking answer. Identify the connection ID of that request.
Select all events.
Filter DNS requests from apple.com subdomains by entering the following text in the search dialog of the column query
.apple.com
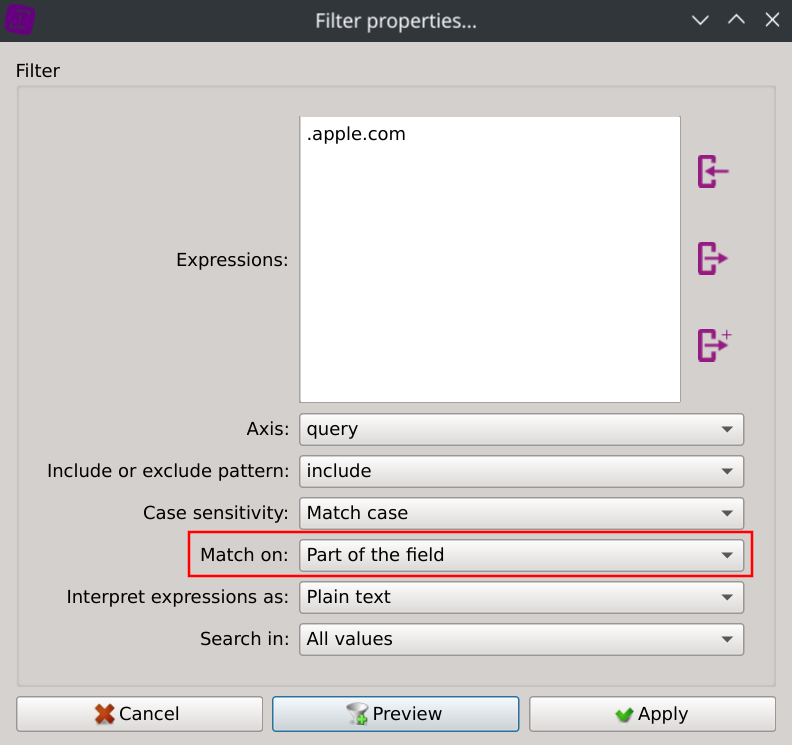
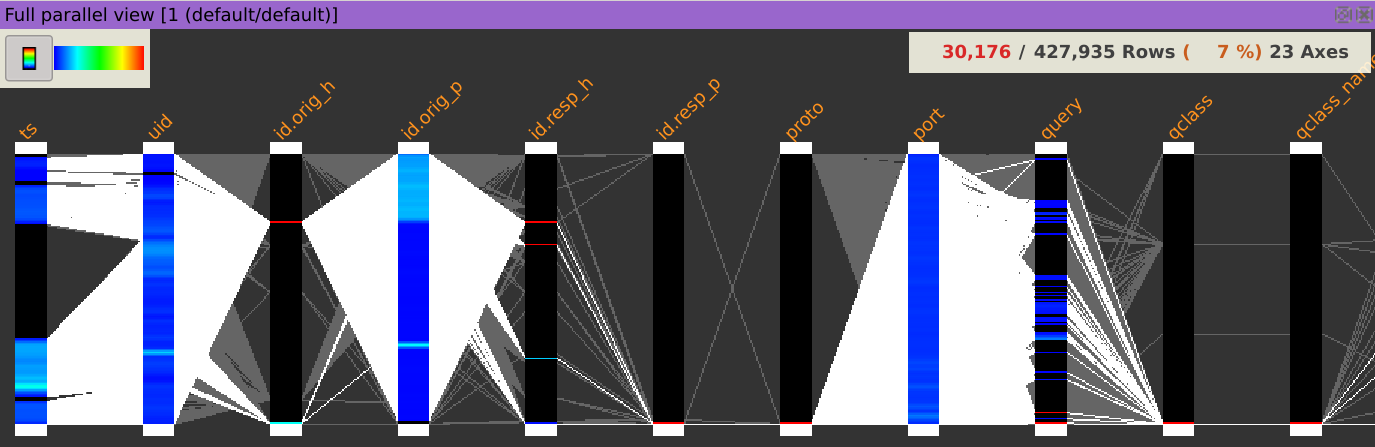
Show DNS requests answers by displaying the Distinct values dialog of the answer column.

Isolate the suspicious-looking answer by clicking on it.
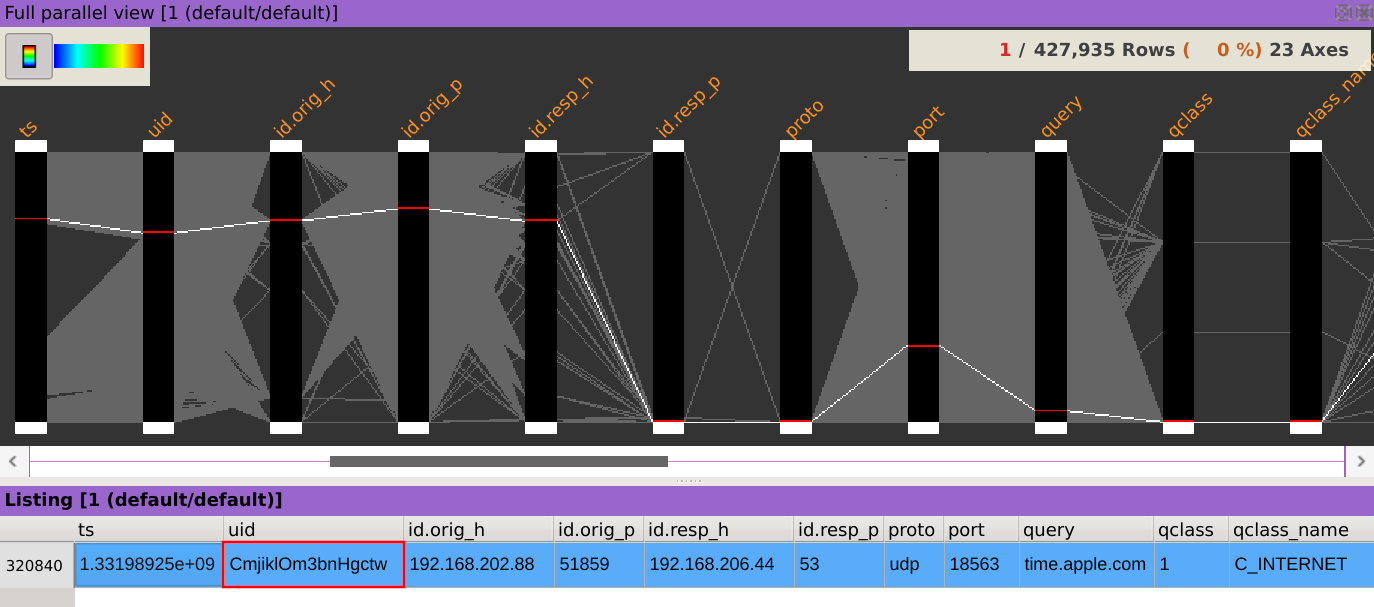
The column uid is displaying the connection ID of the request.
Answer: CmjiklOm3bnHgctw
